HAVE ASSURED ALL-ROUND SECURITY FOR YOUR BUSINESS WITH OUR WEB SECURITY
Partners
While setting up your projects over the internet, it is really important to make sure that the cybersecurity policies are strong enough and the firewalls are in the right place so that nobody can breach the data and steal it. We ensure utmost security for your business with our meticulously chosen cybersecurity measures.
Cyber Security is really important as many organizations collect, analyze and store data over multiple devices. These data may be company sensitive and contain financial data or personal information about any employee or client and if this information gets into the wrong hands, it can create havoc within the company.
According to 2017 Cybercrime Report by Cybersecurity Ventures, Cybercrime damages will cost the world $6 trillion annually by 2021.
The Equifax breach in 2017, affecting 143 million customers, has been reported to exceed the largest publicly disclosed hacks ever reported.
Our security implementation team works on securing your communication within and outside the organization. We believe that any communication within the organization and with its clients should be highly secure. Keeping that in mind, we have designed an advanced encrypted communication channel/platform for organizations of any size and industry to implement and use immediately.

We identify what is vulnerable and prone to malpractices in your business and ensure high security of those vulnerable areas. We detect those vulnerabilities with penetration testing.
Examining employees’ commitment and making them aware of security policies is what we do through the social engineering test. Employees should not get manipulated by malicious sources and leak confidential information.
We identify various factors of business like employee actions,business activities, position, size, etc., and make sure they are complaint with company’s security policies. The product being developed should comply with the specified requirements, including the security requirement. Compliance assessment helps to identify areas of potential risks.
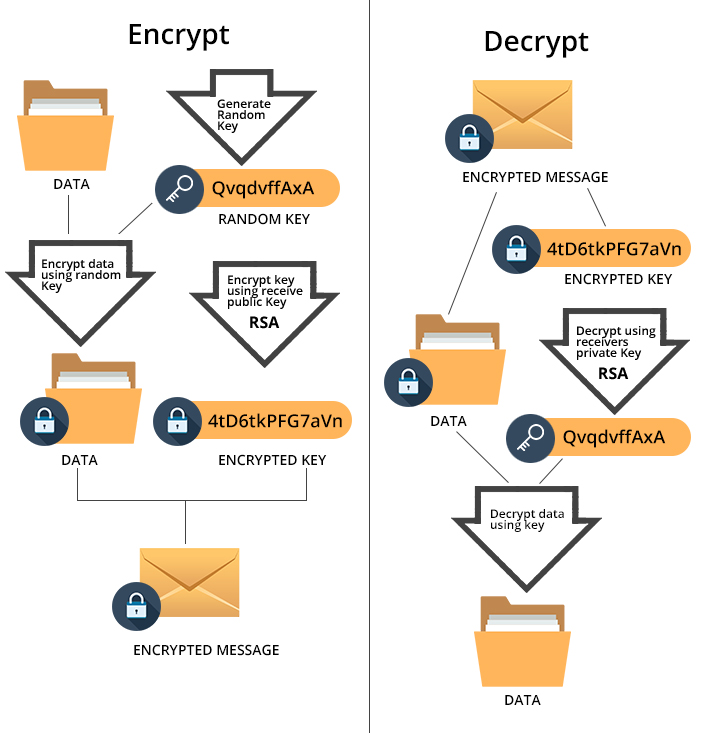
We are using PGP backed by RSA keys to encrypt the messaging. We encrypt and decrypt the messaging on the client side and hence none of the plain text messages are transmitted over the internet. To protect customer devices, we use few extra layers of authentication by device key, location key and social key (a patent pending concept).
It is better to be safe than sorry. Investing in the security of business is never a loss. We assist companies to optimize their security investments by identifying the correct security measures.
We have designed the solution to work with Android, iOS and all types of computers including laptops, desktops and tablet pcs.
We have well-defined processes for every function that ensure successful development and smooth delivery. Over the years,